

This content is for educational purposes only and should not be considered financial advice. Crypto investments carry risks, including loss of capital. Always do your own research or consult a licensed advisor before investing.
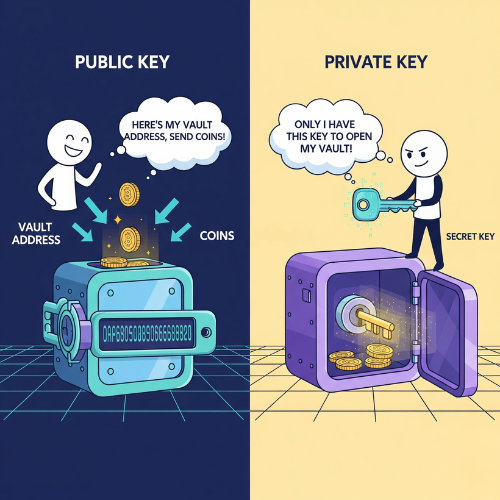
In cryptography, a public key is a visible digital identifier used to receive data or verify signatures, while a private key is a secret code used to sign or unlock transactions. Together, they form a pair that enables secure encryption, authentication, and ownership in systems like cryptocurrencies.
Public and private keys are part of asymmetric encryption. Instead of one shared password, you have a pair of mathematically linked keys.
When someone encrypts data with your public key, only your private key can decrypt it. This ensures confidentiality and authenticity.
Public key cryptography was first introduced in the 1970s by Whitfield Diffie and Martin Hellman, followed by the RSA algorithm. Before that, all encryption relied on shared secret keys, which were hard to distribute securely.
Today, the system is everywhere: it secures online banking, HTTPS websites, email, and, of course, blockchain transactions. Without public/private keys, the modern internet could not function safely.
A public key is a long alphanumeric string derived from the private key. It is safe to share because it cannot be reversed to reveal the private key.
In crypto, the public key (or its shortened form, the wallet address) lets others send you funds. In digital communication, it verifies that a message truly came from the claimed sender.
The private key is the most sensitive piece of cryptographic information. It is generated randomly and must be stored securely. Whoever controls the private key controls the funds or data linked to it.
In blockchain, losing your private key usually means losing access to your crypto permanently. This is why wallets, backups, or advanced methods like MPC (multi-party computation) are used for safety.
Public/private key pairs are not only for crypto. They protect a wide range of digital interactions:
These examples show that asymmetric cryptography is a universal tool, not limited to finance.
While key pairs are extremely secure, risks exist when users mishandle them:
Understanding these risks makes private key protection a top priority.
There are several ways to keep your private key safe, each with different levels of convenience and protection. The most common is a non-custodial wallet, where only you control the keys. For stronger security, hardware wallets store keys offline, making them resistant to hacks. Some users rely on paper wallets, writing or printing keys on paper and keeping them in a secure place. More advanced methods include multi-signature (multisig) wallets, which require multiple approvals before funds can move, and MPC (multi-party computation) wallets, which split a key into encrypted parts stored across devices or servers. Cloud backups with strong encryption, password managers, or biometric protection can also add layers of safety, but they should never replace secure offline storage.
No. A public key is designed to be visible. Its purpose is to allow others to interact with you securely. What must always remain secret is the private key.
Anyone can hold or copy your public key. It’s meant for distribution so others can send you encrypted data or cryptocurrency.
Yes, exposing your public key is safe for your funds. However, reusing the same public key in some blockchains may reduce privacy since others can trace your activity.
The term refers to the open half of an encryption pair. It allows others to initiate secure communication with you, knowing that only your private key can complete the process.
Public and private keys are the backbone of cryptography. The public key is for sharing; the private key is for protection. Together, they enable secure communication, online privacy, and true ownership in crypto.
Want to keep your crypto safe without complexity? Explore Bleap’s non-custodial wallet
The public key is shared to receive data, while the private key is secret and used to sign or access it.
No. It is safe to expose and is designed to be public.
Anyone can hold or copy it, but only you should hold your private key.
Yes, but never expose your private key.
It means the visible half of a cryptographic pair used for secure communication or transactions.
Features
Improvements
Bug fixes